|
Experiment V: Dynamic routing - RIPAhmet Sekercioglu and Leon Seng |
Objectives
We will learn how Routing Information Protocol works by investigating the convergence of the routing tables over time. We will also learn packet processing basics by using the Scapy packet manipulation and analysis tool.
Experiment
RIP Implementation in Mininet
Chapter 18 of [dor19] has a slightly simplified (no poison reverse or triggered updates) but a quite realistic Routing Information Protocol (RIP) implementation.
The implementation is in the Python3 file rip.py. We run it in each router participating in the distance-vector routing table updates. We quote the operational summary of the algorithm from the book as follows:
Most of the time, the program waits to read update messages from other routers. Every UPDATE_INTERVAL seconds the program sends out its own update messages to the neighbours. The update messages are placed in UDP packets, and sent to a special IP multicast address: The official RIP multicast address 224.0.0.9. Port 520 is used for both sending and receiving.
To keep the implementation simple, rather than creating separate threads for receiving and sending, a short (one second) recv() timeout is configured, and then after each timeout we check whether it is time to send the next update. An update can be up to one second late with this approach, but this does not matter.
The program maintains a “shadow” copy RTable of the real system forwarding table, with an added cost column. The real table is updated whenever a route in the shadow table changes. In the program, RTable is a dictionary mapping TableKey values (consisting of the IP address and mask) to TableValue objects containing the interface name, the cost, and the next_hop.
You can refer to Section 18.5 of [dor19] if you would like to learn more about the implementation details.
Convergence of RIP
We will use the topology we have been using in our distance-vector algorithm lectures (instead of letters to idenfity the routers we use numbers though to make scripting the topology easier):
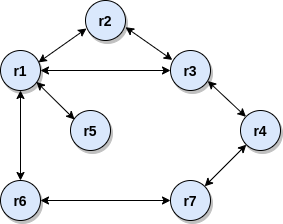
Download the script pd_7_router_net.py and the RIP implementation rip.py.
Start the network: sudo python pd_7_router_net.py
ping test from r1 to r4 (it should fail, confirm this)
start capturing packets on r4:
xterm r4, then run
tcpdump -i any -s0 port XXX -w r4.pcap at the xterm screen
where XXX is the port number that RIP routing update packets are sent to.We will now start running the RIP on some routers to allow ping packets from r1 to r4 successfully delivered. Do not start running the algorithm on all routers at once. What would be the route involving most hops connecting r1 to r4? Start running the algorithm only on these routers. In order to run the algorithm on a router do the following: first open an xterm command window on the router of interest: xterm rX, and then at the xterm screen run: python rip.py &.
How many seconds passed until the ping test starts working?
Examine the pcap file using Wireshark.
How many routing table changes do you see?
What does metric = 1 mean?
Now start running RIP on all the remaining routers.
Check the pcap file again. How many routing table changes do you see?
Terminate the Mininet network, we will start it again for the next stage of the experiment.
Packet Analysis with Scapy
As we mention above, Scapy is a software tool for packet manipulation and analysis. It allows one to send, sniff, dissect and even forge network packets. we will only use its packet analysis capabilities. Here are some useful functions:
- rdpcap
Reads a packet capture (pcap) file and returns a list of packets.
- packet.getlayer(protocol, n)
Returns the
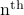 field of a protocol in the packet. E.g. getlayer(RIPEntry, 3) will return the third RIP entry in an RIP update packet.
field of a protocol in the packet. E.g. getlayer(RIPEntry, 3) will return the third RIP entry in an RIP update packet.
See parse_rip.py for extracting information from a RIP packet. For further information you can refer to its documentation.
Now, we are ready to examine some packets:
Modify pd_7_router_net.py to start capturing packets on all routers before RIP starts running. Make sure to name each pcap file differently. Reminder: Starting a command on a node looks like this: rX.cmd(f“command &”)
Start the network: sudo python pd_7_router_net.py
Open xterm command windows to each router and start running RIP on the routers.
Let the network run for a few minutes.
Write a Python script to parse each packet capture file to print the routing table for each router in the following format
R1 (time) IP Netmask Metric NextHop 172.16.34.0 255.255.255.0 4 172.16.13.3 ... ... ... ... ... ... ... ...
Don't forget to show the running script to your lab demonstrator.
Your Report
After finishing your experiments, you will need to prepare a short (maximum two pages, 10 pt Times-Roman font) report summarizing the key points you have learned in this exercise.
Please convert your report to PDF (no other formats will be accepted), zip your report with all the Python code you have written for the experiment, and upload all as a single zip file to the unit's Moodle site before the due date (we will post the deadlines at the unit's Moodle site).
References
[dor19] P. Dordal, An Introduction to Computer Networks (free access).
[lut13] M. Lutz and D. Ascher, Learning Python (Monash Library access).
[pet19] L. Peterson and B. Davie, Computer Networks: A Systems Approach (free access).
[rho14] B. Rhodes and J. Goerzen, Foundations of Python Network Programming (Monash Library access).
[sar14] M. O. F. Sarker, Python Network Programming Cookbook (Monash Library access).